Dude, For Real -- Encrypt Your Web.Config
After I released my web.config encryption utility I expected the world to transform into a Utopia of protected web.config files and happy developers. However, shortly after the tool was released I actually received some disagreement about the usefulness of web.config encryption.
Based on some other comments I received I got to thinking -- I not sure that some people realize how possible it is to lose a web.config from a simple programming mistake.
But The Web.Config Is Safe -- Right?
Sure, your web.config is safe by normal means. Just try it - find an ASP.NET website and just try to browse to their web.config file -- See! it's safe!!
True, your web.config is safe - but what about a programming mistake? Those never happen, do they? Are you sure?
One of my favorite examples is the file download. Sometimes we want to serve up content as if it is a download instead of showing it in the browser. That said, here is an ASP.NET MVC example of why you ought to go on ahead and encrypt that web.config file just to be on the safe side.
//MVC Action to download the correct file From our Content directory
public ActionResult GetFile(string name) {
string path = this.Server.MapPath("~/Content/" + name);
byte[] file = System.IO.File.ReadAllBytes(path);
return this.File(file, "html/text");
}
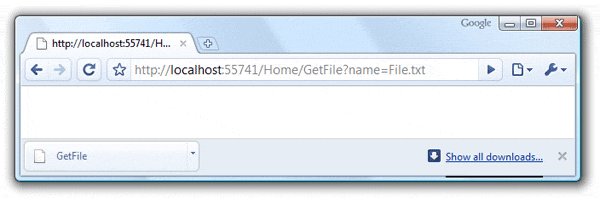
Seems reasonable enough - Other than error handling, do you see anything that looks out of place with this code? We map to the correct directory, we get the bytes for our file and return them to the visitor -- You can even try it out.
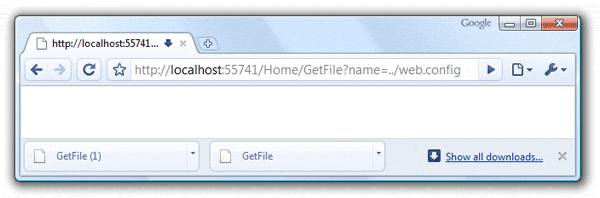
Cool, see how our file downloaded - Works great! But let's be a little sneaky and play with the URL at the top. How about we do something like...
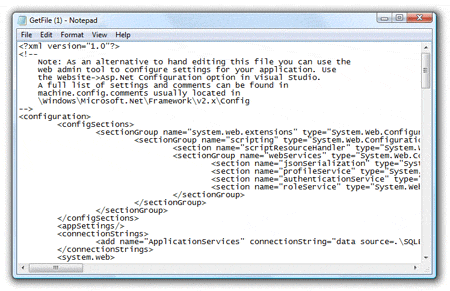
Did you just get a sudden feeling of dread? Did you just shout 'Oh Snap!' loud enough that all your peers are staring at you? What do you suppose is in this file we just downloaded? I'll give you three guesses, but I'm taking two of them away...
It's not hard to miss something -- after all that's why it's a bug, because if we thought of it then it wouldn't be there to begin with. Web.config encryption == cheap insurance.
Prying Eyes
I got this comment the other day and it was absolutely brilliant -- Rob Thijssen wrote...
Encrypting configs in enterprise applications is definitely worth the time. Many companies allow contractors access to source code repositories that contain unencrypted configs that contain credentials which can be used to gain access to sensitive information. I have seen implementations where credentials were available to hundreds of developers that could give any one of them access to thousands of credit card details...
And he's absolutely right. Do you want just anyone passing through the directory to have access to read the sensitive data inside your web.config? Just because they didn't have hack into your server doesn't mean they need to be reading the passwords to your SQL servers.
Dude, For Real -- Just Do It
Web.config encryption only takes a couple moments and provides much more security than a clear-text file. It may not be enough to thwart a hacker that has full access to your entire server, but if you ever have that 'uh oh -- someone just downloaded my web.config' moment, then at least you know you're covered.
July 22, 2009
Dude, For Real -- Encrypt Your Web.Config
Post titled "Dude, For Real -- Encrypt Your Web.Config"
 hugoware.net is licensed under a
hugoware.net is licensed under a